What a Solution to Pig Butchering Scams Must Look Like

The signals for pig butchering crypto scams are there. They just aren’t being analyzed.
Pig butchering scams are no longer fringe fraud. They are industrialized, AI-accelerated, and built to exploit human trust.
Since the start of 2025 alone, custodians have seen $12.24B siphoned away through social engineering campaigns that play out over weeks or months.
These scams are winning not because the signals aren’t there, but because the tools custodians use aren’t designed to see them in time—or act with confidence if they do.
A realistic fear of serving users a false positive is “silent user churn.” Only two out of ten scam victims report fraud, and the remaining eight often churn, costing custodians lost revenue opportunities.
Why current tools fall short
Static rules miss slow-burn scams
Most custodians still rely on static, pre-set triggers—like hard-coded thresholds for transaction size, speed, or withdrawals to known bad addresses—to detect fraud.
These rules were built for obvious, one-off theft, not the incremental authorized transfers that define pig butchering scams.
- Velocity and size thresholds overlook pig butchering flows, which move modest amounts over weeks to avoid suspicion.
- Static blacklist checks can’t keep up with new scam addresses that have no onchain history when used.
- One-time address matching fails when scammers rotate wallets after each use — a tactic so common that an address may be abandoned minutes after receiving funds.
If a scam doesn’t look like fraud according to these legacy triggers, no incident is raised — even when multiple detectable scam signals are present elsewhere.
Data blindspots mean half the scam signal is ignored
Legacy tools look almost exclusively at onchain transaction data. That leaves entire categories of scams invisible—from offchain signals like scam websites and social campaigns to fraud-as-a-service account patterns that could reveal a coordinated fraud ring.
Critical missing inputs include:
- Offchain threat intelligence—scam websites, phishing fingerprints, hosting metadata, and social media listening.
- Fraud-as-a-service behavioral linking—correlating seemingly unrelated addresses participating in the same scam.
- Early-onchain behavior patterns—such as scammer-controlled wallets funding multiple new addresses (gas-funding cycles) or quick-hop transfers to funnel wallets.
When these signals aren’t captured, valuable fraud indicators are ignored because legacy approaches are unable to build and manage the datasets.
False positives paralyze early response
With more than 25% of cases turning out to be false alarms, fraud teams often invest time in finding conclusive proof before acting. The hesitation gives scammers the time they need to expand their theft — and ensures the funds are never reclaimed.
When detection is based on partial or noisy data, alerts are harder to trust, and fraud teams face a dangerous choice:
- Block a flagged transaction and risk alienating a user making a benign transaction, OR
- Wait for conclusive proof, allowing the scam to escalate in the process
Most choose the latter. This “false positives paralysis” means early-stage fraud is rarely recorded, and prevention opportunities are ignored.
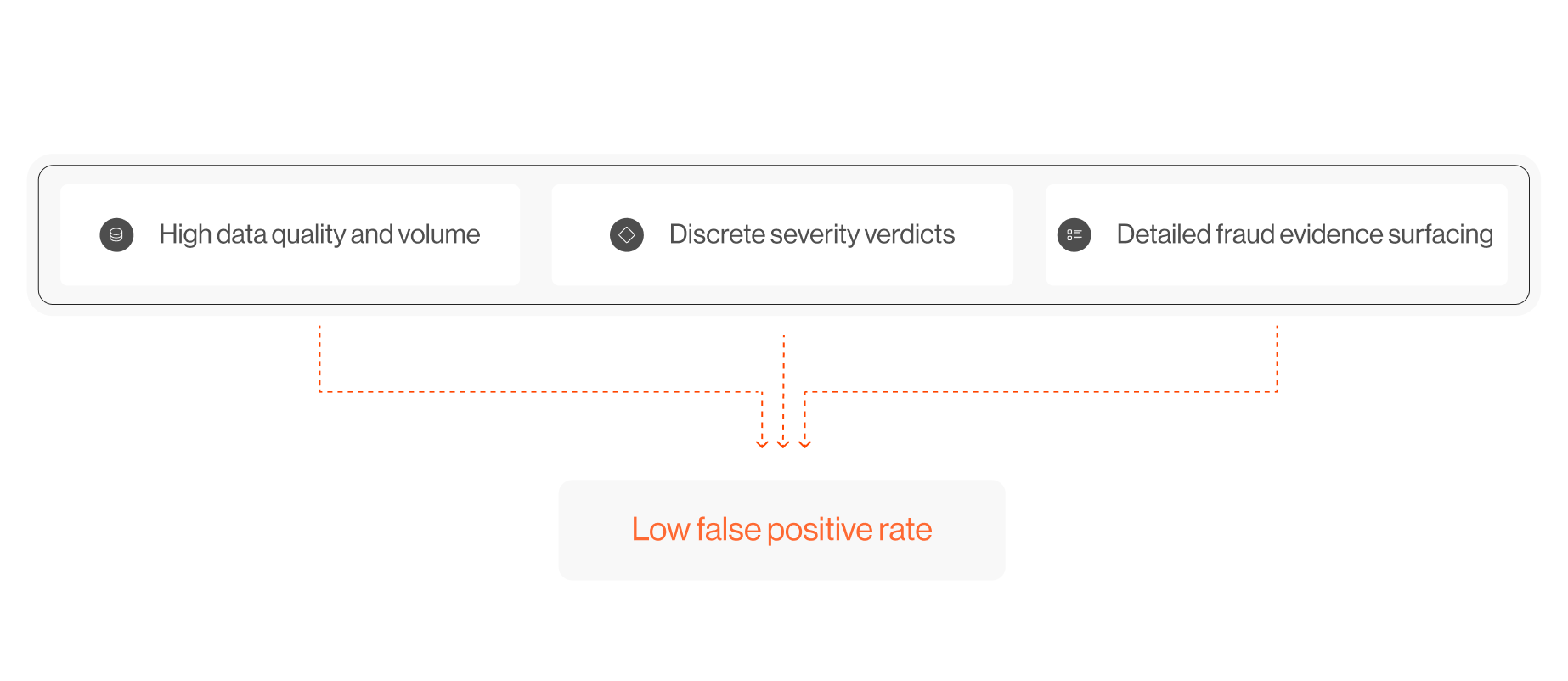
What a modern fraud solution must offer
The requirements for solving pig butchering scams and other social engineering campaigns are clear. Detection tools that can’t fulfill demanding requirements must be categorized as legacy solutions.
- Detect intent without onchain address history
Must support fresh crypto addresses, which, with the help of scam automation and AI, make up a large majority of investment scam activity - Link onchain and offchain intelligence
Real-time signals from new scam websites, hosting metadata, and social media campaigns. - Spot patterns across addresses and infrastructures
Correlate seemingly unrelated accounts, wallets, and domains that belong to the same fraud campaign and do so across multiple chains. - Surface evidence, not just alerts
Give fraud teams a “why” to act faster—with compliance-grade proof and context. - Reduce false positives without missing true threats
Precision is key to prevention to maintain user trust.
Closing thoughts
Most fraud prevention tools were built for yesterday’s threat landscape. Until they meet these requirements, custodians will continue to lose billions to scams they could have stopped — and their users will keep walking away without a word.
Prevent Crypto Fraud with Blockaid
Blockaid’s Crypto Fraud Prevention (CFP) solution moves custodians left of boom—detecting and stopping scams in real time, directly in the custodial app UX.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




