Malicious dApps 101: Wallet Drainers

Intro
We’ve devoted our professional lives to tracking malware, first within Israel’s elite Unit 8200 for cybersecurity and now within web3. While there are differences between traditional security and web3 security, we see even more similarities.
That might sound surprising. Whereas in web2, it’s all about securing code execution—via activities such as static scanning of binaries on disk and dynamic tracing during load and runtime—web3 revolves around transactions. But transactions are actually about much more than just transferring assets. Whenever someone initiates or receives a transaction, they are essentially executing code, much like how a program runs on a personal computer.
Unfortunately, then, just as web2 is rife with malicious code, malicious applications (or dApps) are everywhere in web3—we’ve seen them pop up on Google Ads, NFT marketplaces, and Discord. Moreover, despite the transparency that blockchains provide, humans aren’t able to easily determine whether the given code is malicious. Without tools, web3 users are vulnerable to malware that can drain their crypto wallets.
We want to make transacting in web3 as secure as opening a file on your computer or paying with your credit card on Amazon. This article aims to explain the characteristics of wallet drainers and why even the savviest crypto users need to be careful.

At a quick glance, it can be difficult to differentiate between a real website and a scam
What Is a Wallet Drainer?
To understand a wallet drainer, you have to first understand a bit about how decentralized applications, or dApps, are architected. A dapp is essentially a regular web application that connects to your wallet. When you connect your wallet to a dapp, you are authenticating yourself and allowing the dapp to perform various operations that involve reading and writing the state of the blockchain. For instance, a dApp can enable you to mint a new token.
The problem arises from the level of trust that must be extended to a dApp. A dApp that offers to mint a free token can indeed carry out this action for the user. However, it can also drain your wallet by deceiving you into signing a malicious transaction.
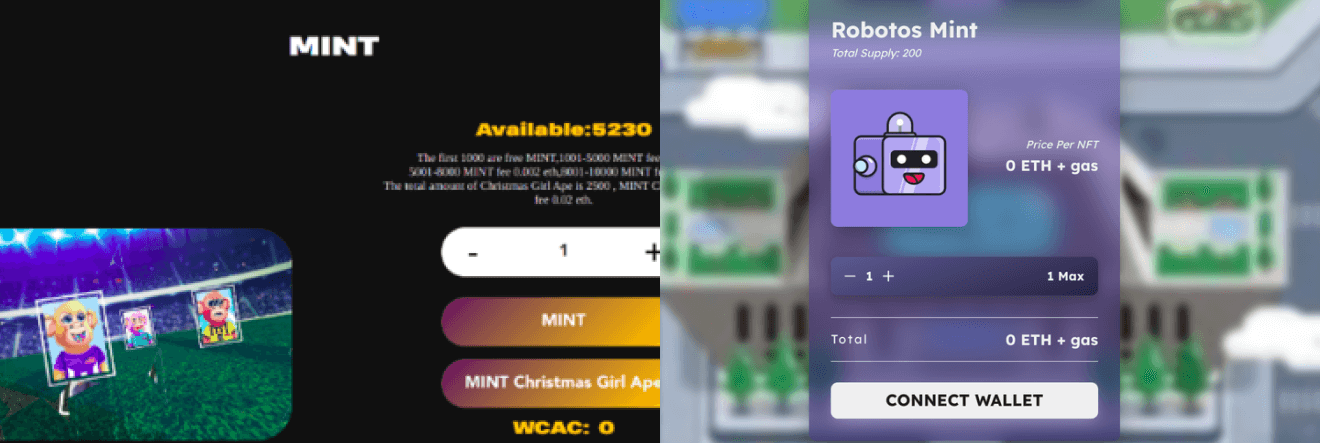
Can you spot the wallet drainer? On the left, a benign minting site; on the right, a wallet drainer.
New examples emerge everyday. Some target individuals by hacking social media accounts. Other wallet drainers are covertly injected into well-known dApps. Ultimately, malicious dApps typically share three main characteristics: impersonation, distinctive patterns of use for web3 APIs, and malicious transactions and signatures.
Impersonation of a brand or personality
Most wallet drainers try to emulate or impersonate a known brand in order to lure a user into entering and interacting with an application.
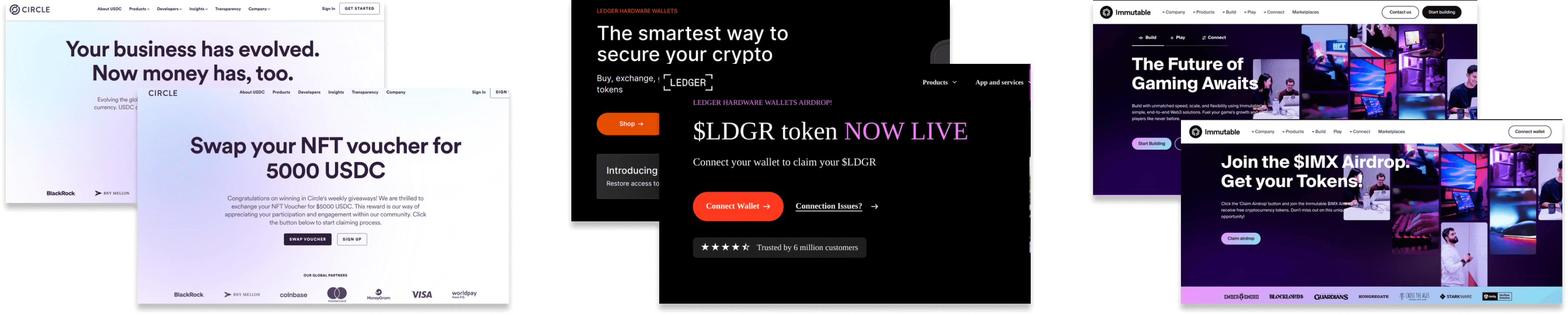
Wallet drainers impersonating well-known brands - at the back, the original site; at the front, an impersonating drainer - Immutable, Ledger, Circle, from left to right.
Distinct Pattern of Web3 API Usage
To count the victim's assets and determine how to discreetly extract maximum value from an address, most wallet drainers rely on web3 APIs. These APIs encompass a range of sources, including, for example, OpenSea's API for obtaining information on NFTs held by the victim and the Moralis API for retrieving data on token positions and dollar prices.
The tricky part is that the use of these APIs is common practice; many popular and legitimate dApps utilize them as well. What sets wallet drainers apart is the distinct patterns in their API usage. Fortunately, we can scan for these patterns to detect wallet drainers.
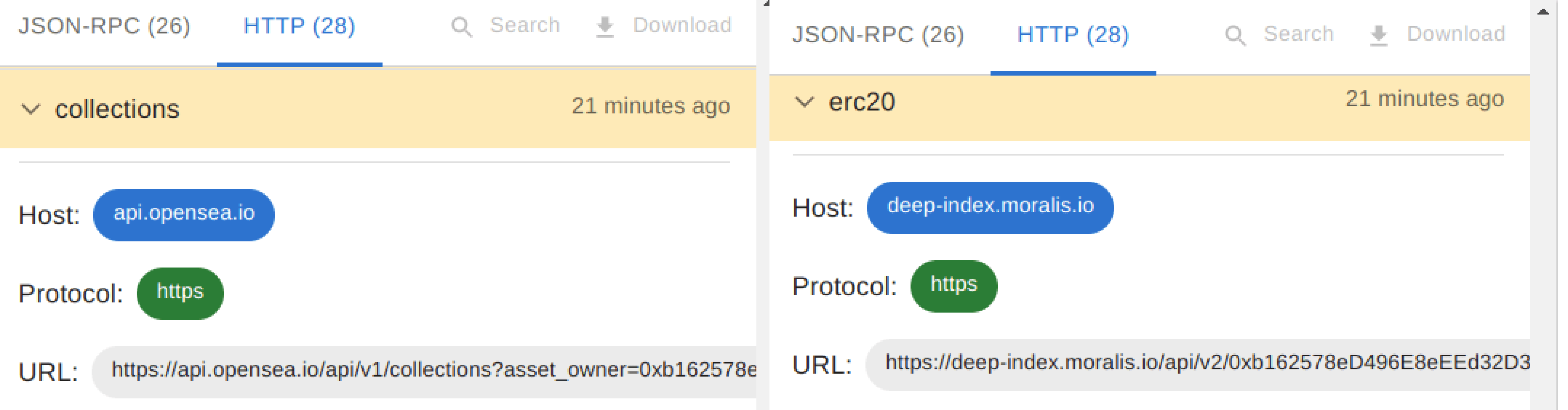
Web3 APIs used by wallet drainers: on the left, the enumeration of the victim's assets using the OpenSea API; on the right, the utilization of the Moralis API to enumerate the ERC20 tokens held by the victim.
Malicious Transactions & Signatures
The ultimate goal of every wallet drainer is to obtain transactions and signatures from the user. These are the means through which they can steal assets from the victim's wallet. The challenge for these drainers is to accomplish this without arousing the user's suspicion; they need users to sign these transactions without hesitation.
Attackers adapt quickly and adjust their techniques as new technologies are deployed in the web3 ecosystem. For example, we’ve observed attackers transitioning from attempting direct asset theft through transfers or approvals to using more covert methods involving interactions with OpenSea Seaport contracts, token permits, Blur, and decentralized platforms like Uniswap and PancakeSwap, among others.
Attackers aim to make the user experience of signing malicious transactions appear as normal as possible. For instance, a user who receives a Blur order to sign might think, "This can't be malicious, as it bears an official Blur signature." Though the signature is indeed official and intended for use with the Blur contract, the attacker can nonetheless exploit it to abscond with all the user's assets.
Case Study: Vitalik’s Twitter Hack
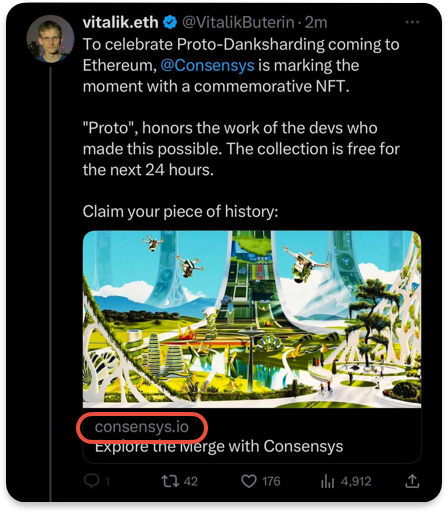
Attackers and wallet drainers do not spare anyone, not even Ethereum co-founder Vitalik Buterin. On Sunday, September 10, the Twitter account belonging to Buterin was compromised by a malicious actor. The hacker executed a successful phishing scam, resulting in the theft of approximately $700,000 worth of assets, by posting a message that offered a limited-time NFT collection minted by ConsenSys. Of course, it was actually promoting a malicious dApp.
Numerous users were lured into the campaign to mint free NFTs. However, the link associated with the post directed them to a phishing website that drained their crypto assets and NFTs from their wallets.
Blockaid successfully detected and flagged the malicious dApp even before its publication on Twitter. This meant that every wallet that integrated Blockaid security was prevented from interacting with the malicious dApp.This achievement was possible thanks to Blockaid's proactive approach, allowing us to identify potential threats in advance, preventing them from becoming active.
By correlating onchain data with various threats observed in the wild by Blockaid's product, we successfully established a link between onchain contracts and addresses associated with prior wallet-draining incidents detected by Blockaid. This approach mirrors the tactics employed by attacker groups: they construct on-chain infrastructure and subsequently deploy it in various iterations to deceive as many users as possible.
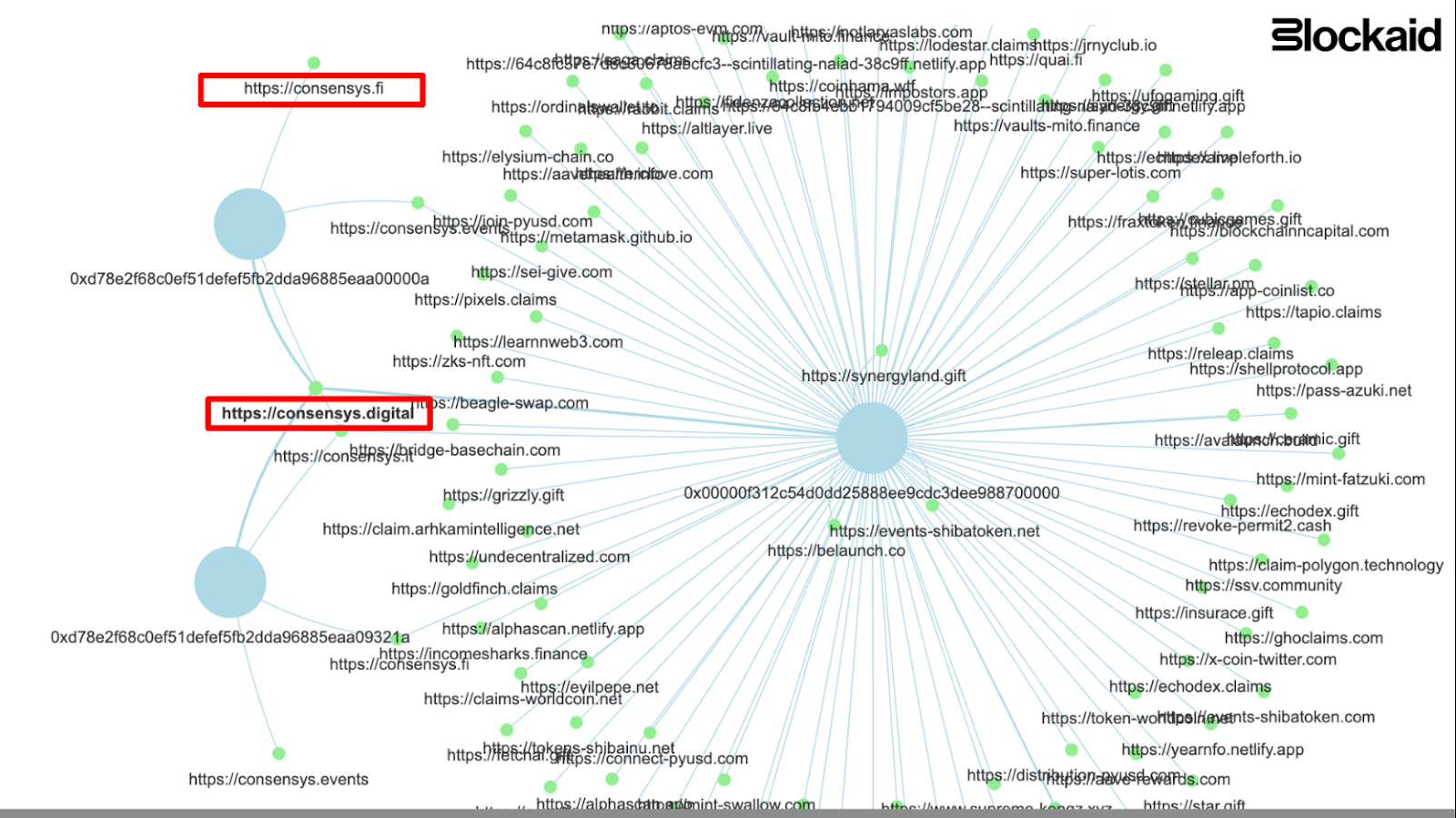
The attack used multiple methods to drain wallets
1. Native Assets Transfer with NetworkController Drainer
The primary contract involved in the hack was located at address 0x00000f312c54d0dd25888ee9CDC3DEE988700000. This contract was active across multiple EVM chains, including Ethereum, Polygon, and Optimism. It essentially functions as a straightforward "withdrawer" contract, with a basic feature that permits specific addresses to withdraw assets from it.
Users who interact with this “NetworkController” contract are prompted to sign transactions labeled "NetworkMerge." Strikingly, these transactions lead to a call to the contract's fallback function, which is not even implemented in the contract. For the user, this seems to result in an inconsequential action, except for the unfortunate outcome of losing their native currency.
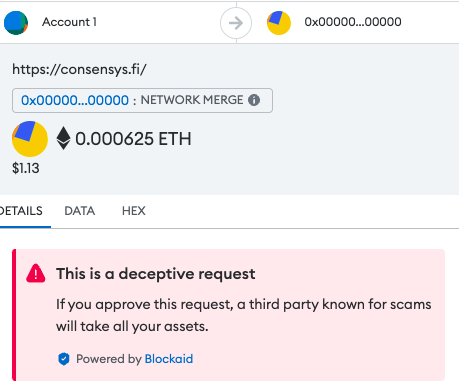
What Metamask Users that had Blockaid enabled have seen while interacting with the contract
2. Malicious usage of Token Methods
The drainer attempted to persuade users to sign approval and transfer requests to illegitimately seize their token assets. The assets were approved/transferred to the address at 0x63605e53d422c4f1ac0e01390ac59aaf84c44a51.
3. EIP-712 Signatures
The drainer utilized offline signatures, particularly EIP-712, to deceive users into surrendering their assets. This included the manipulation of Seaport Orders, Permit Orders, and other offline signatures. The drainer dApp also employed a simulation-based deception method specifically designed for EIP-712, which will be further explained in a subsequent blog post.
4. Employing Dex’s for stealing assets
The drainer leveraged well-known decentralized exchanges such as Uniswap to orchestrate asset-grabbing swaps. This tactic represents yet another instance where the drainer capitalizes on familiar technologies to lull users into a false sense of transaction legitimacy.
Distinguishing between an innocent-but-unfair swap (for instance, someone genuinely transferring assets to another address in exchange for an asset like an NFT) and a malicious transaction is a fundamental aspect of Blockcaid’s detection technology. This capability enables us to identify and flag malicious actors while minimizing false positives on benign transactions.
Conclusion
At Blockaid, we recognize that security stands as a pivotal barrier to achieving widespread adoption in the web3 ecosystem. Our mission is to leverage the knowledge and expertise we've acquired as security experts to further this immensely significant objective. In addition, we are dedicated to sharing our insights and data through articles to disseminate knowledge to both builders and users within the ecosystem.
For end users, we hope this article has shed light on the perils of wallet drainers and serves as a reminder to exercise caution when engaging with applications that are not integrated with Blockaid.
If you're a builder seeking to enhance the security of your product, we encourage you to get in touch with us by signing up for a demo.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




