Building Safely with EIP-7702: How Blockaid Helps Teams Adopt the Future of Smart Wallets

EIP-7702 introduces a major shift in how externally owned accounts work.
Instead of being limited to a single, direct call, EOAs can now be upgraded into smart accounts - effectively granting existing EOAs smart contract functionality.
That unlocks a range of new capabilities - session keys, gas sponsorship, batch execution - all without needing users to migrate to new wallets or upgrade their setup.
It’s a big win for UX and developer flexibility.
But it also introduces new complexity.
The lines between simple signatures and programmable behavior are starting to blur. A single approval could now authorize a dynamic session. A dApp could initiate multiple calls under the hood. Wallets need to show users more than just an address and a gas estimate - they need to explain behavior.
This is what makes 7702 both exciting and challenging. It opens the door to next-generation wallet design - but it also calls for next-generation security thinking.
What It Takes to Build Securely with 7702
EIP-7702 unlocks a wave of new capabilities - but with them comes a sharp increase in complexity and responsibility.
Teams are now expected to implement smart wallet features and manage the new risk landscape that comes with them. Both are nontrivial.
How to support new smart wallet features (without breaking UX)
EIP-7702 brings powerful new functionality to EOAs:
- Batched execution via
wallet_sendCalls - Session keys with scoped permissions
- Gas sponsorship and flexible payment flows
- Temporary smart wallet logic injected via
setCode
Supporting these features requires rethinking how wallets simulate and preview transactions, and how dApps construct session flows across different providers.
For wallets, that means decoding and presenting complex behaviors clearly - without overwhelming users.
For dApps, it means building session logic that behaves predictably, simulates accurately, and integrates cleanly across wallet types.
These aren’t drop-in features. They touch architecture, UX, and trust - all at once.
Managing the New Risks Introduced by Programmable Sessions
With greater flexibility comes new surface area. A single signature can now do a lot more - and that creates room for subtle, high-impact risks.
Examples include:
- Session keys granting overly broad or long-lived access
setCodeused to inject untrusted logic into EOAs- Sponsored flows hiding the true origin of a transaction
- Complex batches mixing legitimate and malicious operations
For teams, the challenge is knowing what’s safe, what needs to be flagged, and how to catch issues early - ideally before they hit production.
EIP-7702 changes what a transaction is. That means wallets and dApps need a new model for understanding and validating behavior - not just calldata.
Blockaid Helps Teams Navigate 7702 - Safely and Confidently
While EIP-7702 introduces new primitives - like temporary smart contract logic and session keys - it doesn’t prescribe how to handle them safely. That part is left to teams building on top.
To support that, Blockaid is providing full 7702 support from day one.Not as a promise - as working infrastructure teams are already using.
Here’s what that includes:
Accurate simulation of 7702 flows
We’ve updated our simulation engine to support all new transaction types introduced by 7702 - including setCode, wallet_sendCalls, and session key usage.
That means teams building wallets can show users exactly what a transaction will do, even if it includes sponsored gas, delegated permissions, or temporary contract deployments.
This also applies to dApps. If you're constructing complex batched transactions or session flows, Blockaid helps you test and preview those transactions before users run into errors or unexpected behavior.
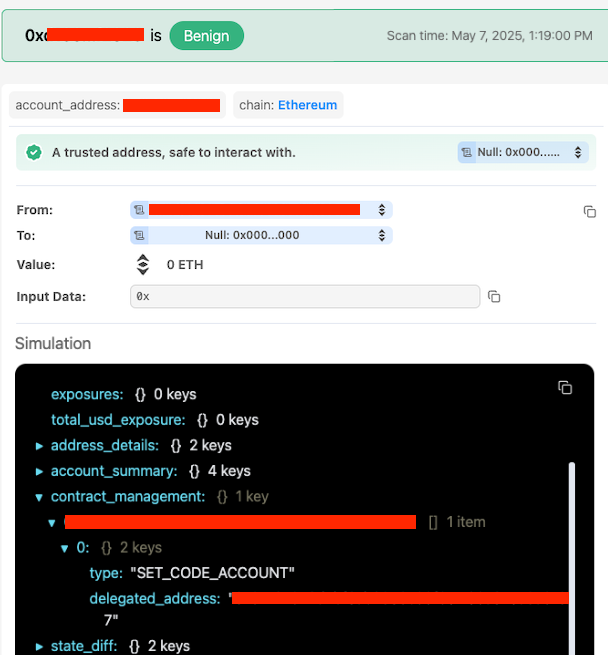
The goal is simple: reduce failed transactions, prevent mispriced gas, and give users visibility into what they’re signing - no matter how complicated the underlying logic is.
Detection of new 7702-specific threats
EIP‑7702 also expands the scope of what a malicious transaction can look like. We’ve already integrated new heuristics and validation steps to catch risks unique to this model:
- Malicious upgrade attacks - where attackers use 7702 to upgrade a wallet into a compromised contract
- Session keys farming and attempt to manipulativly gain excessive scopes or durations
- Hiding malicious behvaiours in complicated batch transactions
- TOCTOU-style attacks that use 7702 features to bypass simulation engines
Blockaid watches for these patterns in real time - at the moment of simulation or signing - and can block or flag transactions before they’re submitted onchain.
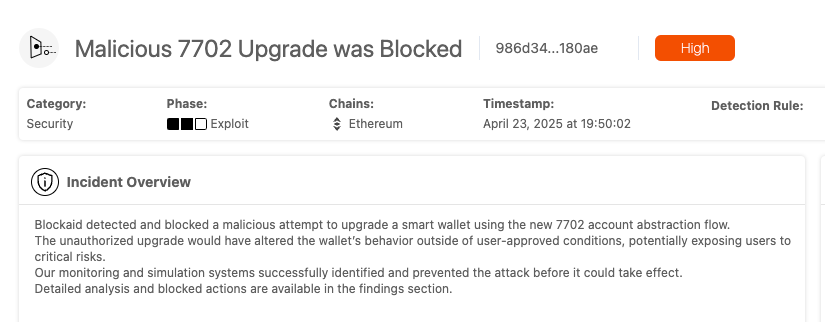
For teams, this means protection against behavior that slips through traditional static analysis or post-facto detection tools.
Dynamic classification of EOAs acting as smart accounts
7702 allows any externally owned account (EOA) to temporarily act like a smart contract. That complicates assumptions many systems make about account behavior.
Blockaid handles this by treating 7702-enabled EOAs as smart accounts during validation. If a transaction injects code with setCode, we classify it, scan the bytecode, and apply the same heuristics we would for any smart contract.
This happens on the fly - without adding latency to the user experience - and ensures your system isn’t blindsided by code execution from an address it assumed was passive.
| Use Case | What Blockaid provides | Why it matters |
| Wallets | Simulation UI components, session key alerts, contract preview logic | Show users what they’re signing |
| dApps and Interfaces | API for modeling 7702 flows, session scope previews, gas estimation | Monitor and audit user flow and provide pre-sign visibility to users |
| Custodians & exchanges | Policy-based cosigner enforcement, session key rules | Teams don’t have to rely on manual reviews |
| Chains & Ecosystems | Threat feed with 7702-specific exploits and live alerting | Allowing ecosystems to detect new threats early |
This is not a separate product. It’s built into the same stack our customers already use.
Conclusion: How Blockaid helps team easily adopt 7702
EIP‑7702 is no longer theoretical. It’s in production. And for most teams, the hard part starts now: integrating new transaction types without introducing regressions, breaking UX, or opening up new attack paths.
Supporting 7702 isn’t just about implementing a spec - It’s about rethinking how users understand transactions, how systems validate behavior, and how teams prevent mistakes that only show up once real users are involved.
The Blockaid team has already spent months working through these challenges with leading wallets and platforms. Not just on security - but on simulation, UX clarity, and system design.
If you're still deciding how to approach 7702 - or if you're already deep in implementation - get in touch today to schedule a call with our engineers.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




