Malicious dApp 101: Wallet Drainers Are Stealthier, More Complex than Ever

In the ever-evolving world of cybersecurity, wallet drainers have emerged as a persistent threat, continuously adapting their tactics to bypass security measures and exploit users. As security protocols strengthen, wallet drainers have evolved from simple scams to sophisticated operations, often backed by governments. This shift towards complexity reflects the increasing difficulty of executing successful scams in cryptocurrency, pushing attackers to develop more complex strategies.
Let’s examine how Wallet Drainers are becoming more and more sophisticated in utilizing web2 technologies to attempt to scam users and avoid detection. Building upon our Malicious dApp 101 series, let’s dive deeper into HOW these malicious actors use web2 tactics to attack web3 users.
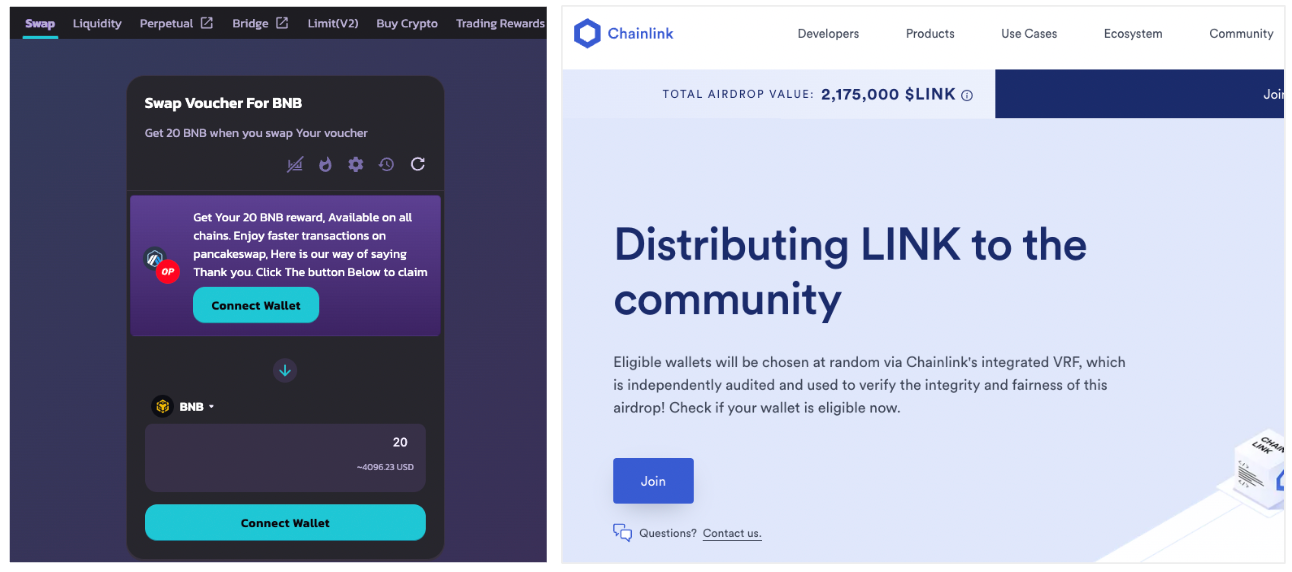
Examples of wallet draining websites
The Stealthy Evolution of Wallet Drainers
To remain undetected and maximize their gains, wallet drainers utilize a range of techniques to conceal their activities and circumvent security barriers:
- Anti-Debugging: Impeding the analysis of their code by employing obfuscation tactics and anti-debugging measures.
- Code Obfuscation: Disguising the true intent of their code by making it difficult to understand and analyze.
- Data Collection: Gathering information about their targets, such as wallet addresses, transaction history, and personal information, to refine and personalize their attacks.
- Managing Attack Logic on Backend Servers: Centralizing the control of their attacks on remote servers, allowing for dynamic updates and remote execution of malicious code.
Now that we’ve got the basics, let’s dive deeper into the web2 intricacies of wallet drainers, examining tactics. Conversely, let’s explore countermeasures that individuals and organizations can and should adopt to protect themselves from these sophisticated threats.
Evading Detection Through Anti-Debugging Measurements and Code Obfuscation
Put simply, the measures mentioned above are designed to hide the true intent of the code and make it difficult for security researchers — and curious individuals — to understand what the code actually does.
Wallet drainers monitor users when they seem to be inspecting the website’s code and behavior - actions such as pressing the right-key or opening Google Chrome's developer tools are being monitored by wallet drainers. If they detect these actions, they may try to navigate the user to a different page, close the tab, or clear the debugging console to evade detection.
Common anti-debugging techniques employed by wallet drainers include:
- API hooking: Intercepting and modifying calls to system APIs to prevent opening Google’s Chrome’s developer tools.
- Debugger detection: Checking for the presence of debuggers on the system and terminating the process if one is detected.
- Code breakpointing: Setting breakpoints in the code to prevent debuggers from stepping through it.
Wallet drainers may also use a variety of code obfuscation techniques to make their code more difficult to reverse engineer, such as:
- Control flow obfuscation: Changing the order in which instructions are executed to make the code more difficult to follow.
- Data obfuscation: Encrypting or encoding data to make it unreadable to debuggers.
- String obfuscation: Encrypting or encoding strings to make them unreadable to debuggers.
Here is an example code taken from a wallet drainer website next to a code snippet taken from a benign dApp:
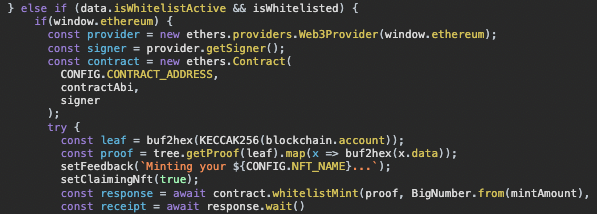
A code snippet taken from a benign dApp
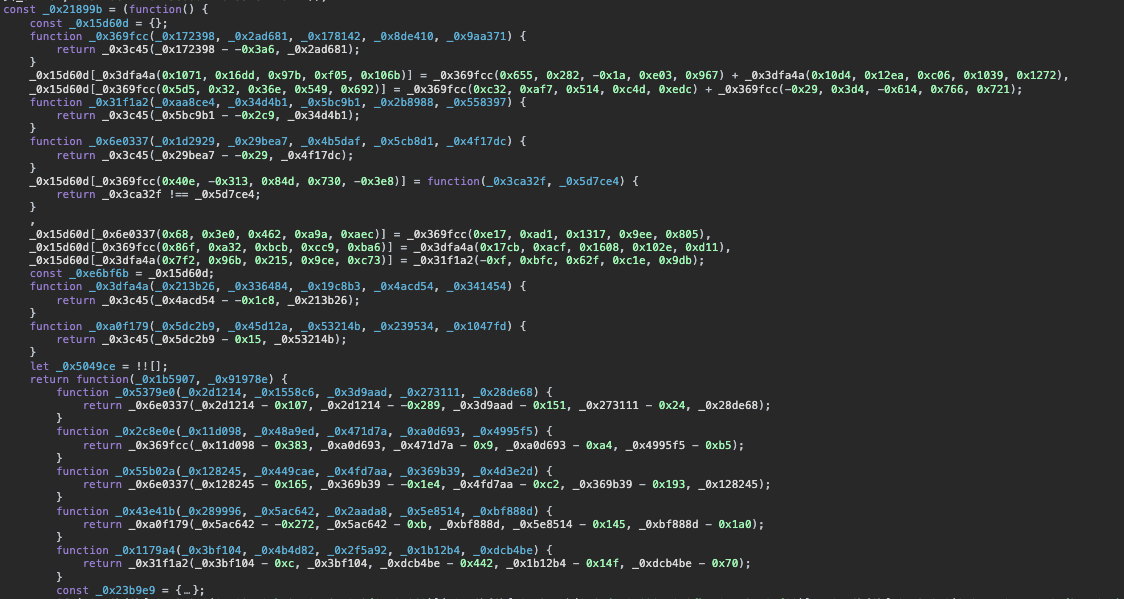
A code snippet taken from a malicious dApp
Comparing the code snippets side by side - there is a notable difference between the two, the malicious dApp tries to hide the intention of its code while the benign dApp is much more readable and accessible.
Managing Malicious Campaigns: Data Collection and Backend Servers
Wallet drainers often use sophisticated data collection and backend server infrastructure to manage their campaigns. These threat actors deploy many websites controlled by a single central server, which collects data about potential victims, such as their wallet addresses, personal information, and the websites they visit.
Wallet drainers use this data to identify new targets, develop more sophisticated attack vectors, and personalize attacks against individual victims. Additionally, the server is used to construct malicious transactions that steal the victim's cryptocurrency.
Wallet drainers use sophisticated encryption techniques to protect their data and communications. Posted below is a decrypted (censored) message sent from a wallet draining dApp to its C2 server:
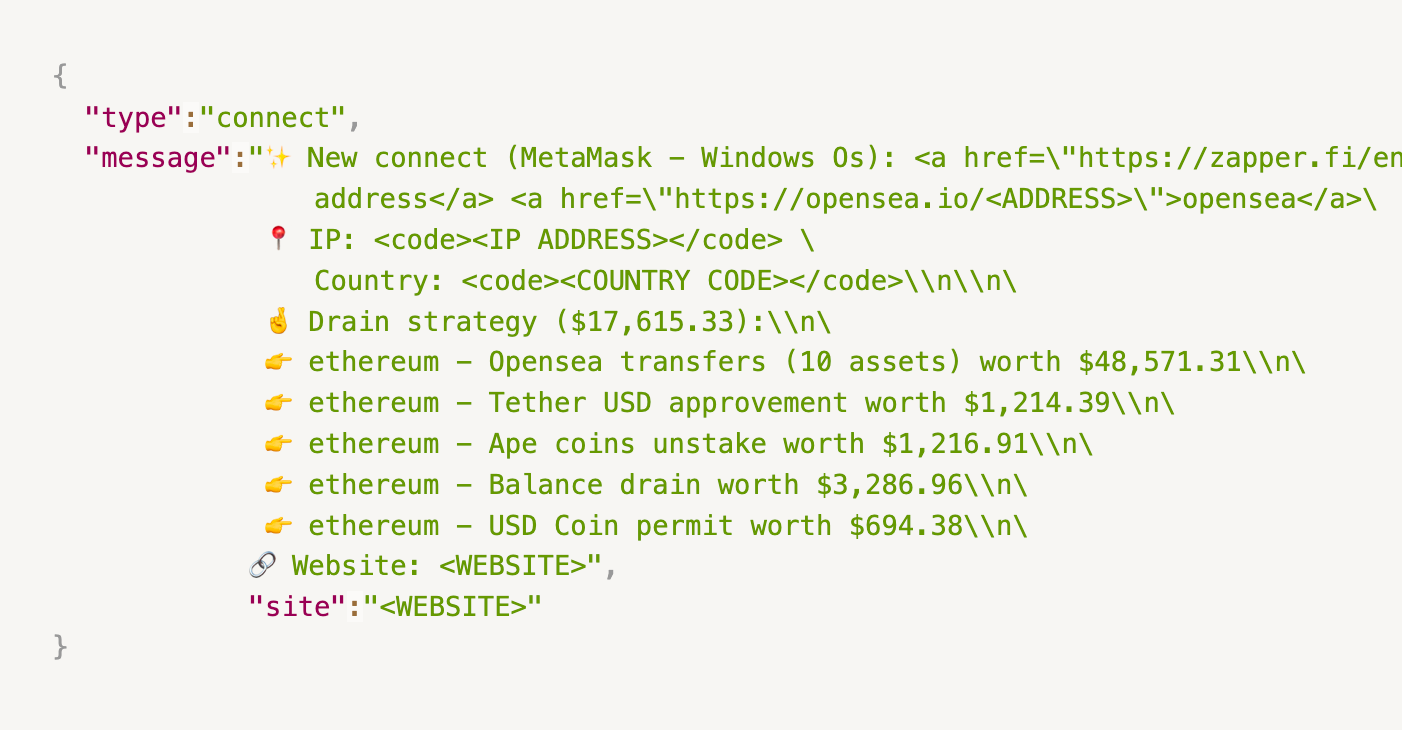
As can be seen, the wallet address, IP, country, assets, and the site that is being visited are logged.
The C2 server constructs a transaction that will yield the highest profit based off the victim’s assets and attempt the victim to sign the transaction - hiding its tactics from clients. Here is a diagram showcasing the communication between a Wallet Draining dApp and its C2 server:
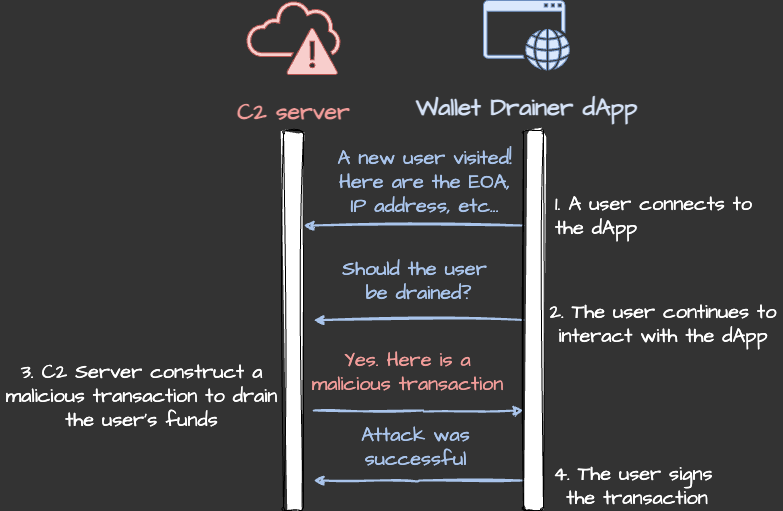
Conclusion
Wallet drainers pose a significant threat to the cryptocurrency ecosystem, and their use of advanced techniques makes them increasingly difficult to detect and prevent. However, by understanding their tactics and tools, we can better equip ourselves to defend against these sophisticated attacks.
Here are some specific steps that users can take to protect themselves from wallet drainers:
- Be wary of unsolicited links and attachments. Wallet drainers often use phishing attacks to trick users into clicking on malicious links or opening infected attachments.
- Visit websites using a VPN or an HTTP Proxy. VPN and proxies can aid in hiding your IP address and additional details that can be collected by malicious threat actors.
- Use Wallets with Blockaid Enabled - Wallet such as Metamask, Zerion and Rainbow that are integrated with Blockaid block malicious transactions and malicious dApps.
The Blockaid research team continuously conducts research on malicious dApps to stay ahead of attackers and catch them before users are affected. Stay tuned for more deep dives into the world of malicious actors in web3.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




