Emerging Attack Vector: Restake Farming

TL;DR - Angel Drainer group has introduced a new attack vector utilizing a protocol to execute a novel form of approval farming attack through the queueWithdrawal mechanism. As we help share impacted wallet addresses, we have also begun to roll out a fix to ensure that all Blockaid-enabled users are protected.
What is Restaking and what is the new technique being used?
Restaking rewards are an incentive provided by EigenLayer, an EVM protocol that enables restaking to extend ETH cryptoeconomic security to additional applications. This allows users that stake ETH natively or with a liquid staking token (LST) to take those staked funds to restake in other applications.
As is often the case with new and innovative technologies, attackers seek to find novel ways to drain user wallets. In this case, the Angel Drainer Group (which is responsible for last month’s Ledger Connect Kit attack) have introduced a novel form of approval farming through the queueWithdrawal mechanism of the EigenLayer protocol.
How does the attack work?
Central to the attack, a user signing a queueWithdrawal transaction effectively approves a malicious withdrawer to withdraw the wallet’s staking rewards from the EigenLayer protocol to an address of the attacker’s choosing. Unlike the regular ERC20 approve method, this is a special kind of approval that is needed due to the nature of Ethereum staking.
From Ethereum Foundation:
Due to how withdrawals from Ethereum are designed, users can only initiate one partial withdrawal per sequential sweep of all validators (which takes approximately 4-5 days).
All funds unstaked from EigenLayer go through a 7-day escrow period before being able to be withdrawn. Thus after you initiate your unstake, you must wait 7-days before being able to withdraw your assets.
Because this is a new kind of approval method, most security providers or internal security tooling does not parse and validate this approval type. So in most cases it’s marked as a benign transaction.
To make it even harder to detect the malicious attack, this attacker uses the CREATE2 mechanism in order to approve these withdrawals to an empty address.
A live example of the attack
Here’s an example for an approval transaction.
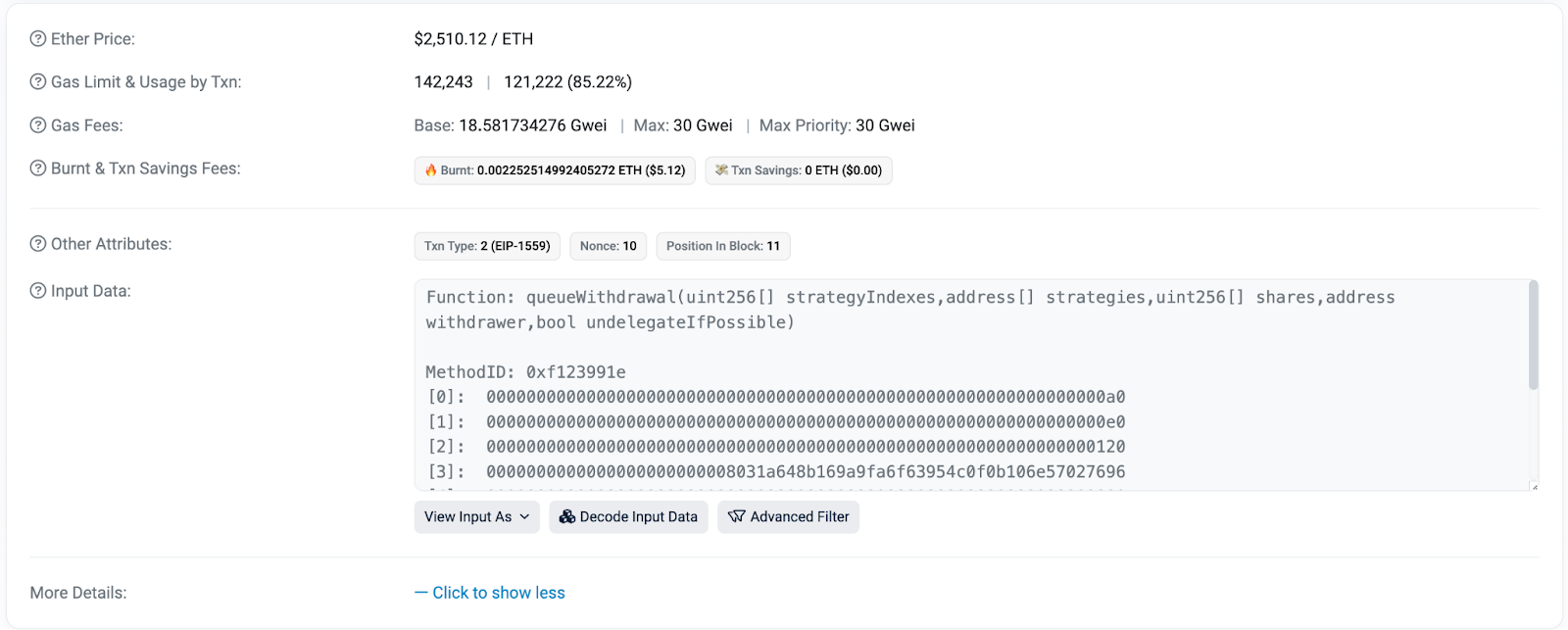
Here’s the draining transaction that took place 14 days after.
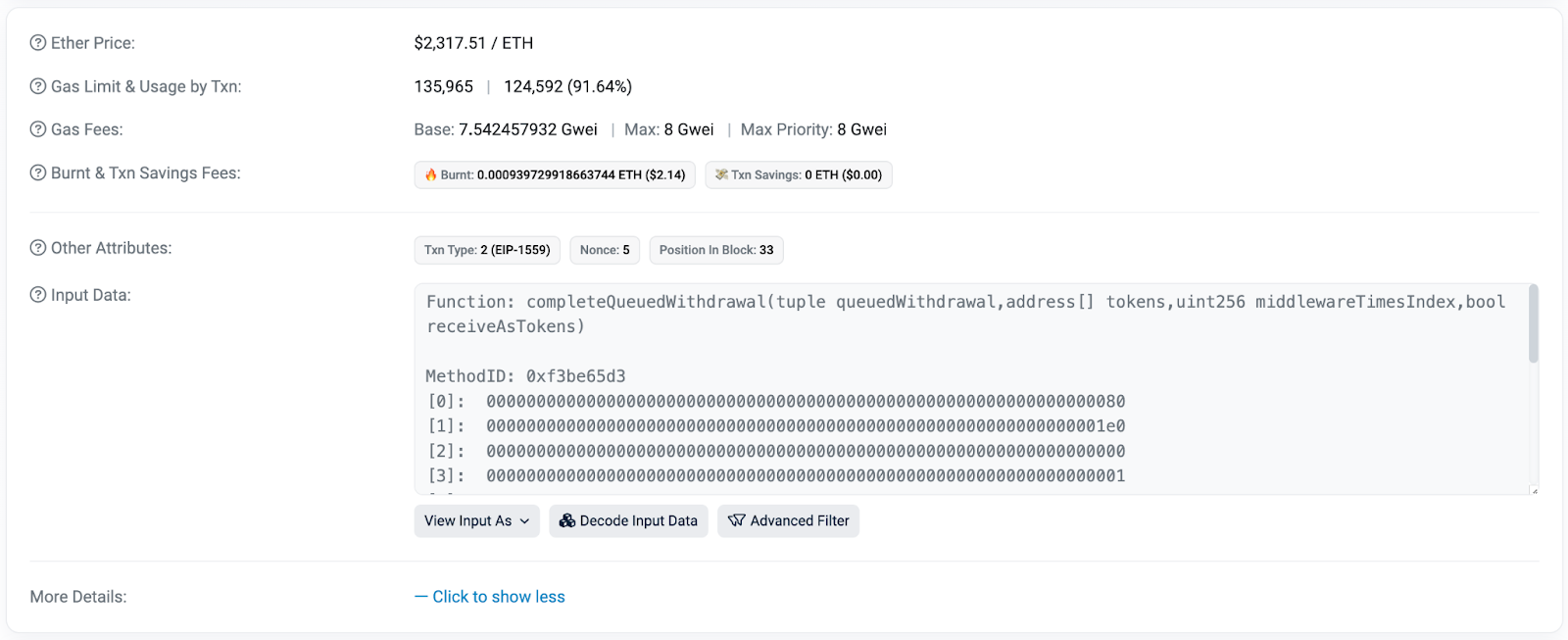
What can we do about it?
For all Blockaid-enabled wallets and dApps, we’re rolling out a fix that will ensure that they are protected from this attack vector. We’ve already contacted the team at EigenLayer to ensure they are aware of this ongoing attack. Let’s get the word out and protect web3 from this new attack vector.
If you’ve been impacted — or you want to see if you have any impacted users — please reach out to Blockaid to learn about how you can keep users safe.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




